ToolShell Exploits Hit US PACER Court System, Canadian Parliament, UK Telecom after 140 Others, Including US Nuclear Entity
CCP threat actors, Warlock ransomware group implicated. The era of the centralized cloud and hybrid environment security is turning into a bonfire.
Microsoft’s on-premises SharePoint servers are currently under widespread, active attack due to a cluster of critical security flaws collectively dubbed “ToolShell”. These include critical vulnerability exploits CVE-2025-49704, CVE-2025-49706, CVE-2025-53770, and CVE-2025-53771. These vulnerabilities affect Microsoft SharePoint Enterprise Server 2016, 2019, and, specifically for CVE-2025-49706 and CVE-2025-53770, the SharePoint Server Subscription Edition. SharePoint Online (Microsoft 365) is not impacted, while the only patch offered from Microsoft so far is for 2016 Enterprise Servers and older, causing continued attacks as recently as Monday.
“While cloud environments remain unaffected, on-prem SharePoint deployments — particularly within government, schools, healthcare including hospitals, and large enterprise companies — are at immediate risk.”
- Michael Sikorski, tchief technology officer and head of threat intelligence for Palo Alto Networks’ Unit 42
The hackers behind the compromises “are bypassing identity controls, including MFA (Multi-Factor Authentication) and SSO (Single Sign-On), to gain privileged access. Once inside, they’re exfiltrating sensitive data, deploying persistent backdoors, and stealing cryptographic keys,” said Sikorski.
Microsoft has found three groups utilizing these four vulnerabilities as a tool/procedure dubbed “ToolShell” - most recognized is Chinese Linen Typhoon (aka APT27) and Violet Typhoon (aka APT31). Another group is a newly observed, previously undocumented cluster called Storm-2603, who Microsoft is tying to Lockbit. "Lockbit Ransomware” is claimed to be majorly targeting Chinese entities, but given LockBitSupp’s pay-for-play Ransomware-as-a-Service model, cause becomes dubious at best. While Microsoft linked this cluster’s activity to potential ransomware deployment, it was unable to assess the group’s objectives. What we seem to be seeing, for now, is observation and exfiltration of data, vs. disruption and destruction of systems and infrastructure storing it.
One group that is coming into the spotlight, and doing significant financial damage, is Warlock Ransomware Group.
The group claimed responsibility for 16 cyber attacks starting in March, including governments. Three of the attacks have been acknowledged:
Information Technology, March 28, Turkey: Bilgi Teknolojileri ve Haberleşme Kurumu.
March 30: Government, education agency, Croatia: Nacionalni centar za vanjsko vrednovanje obrazovanja (NCVVO), March 30.
Critical infrastructure, water and waste authority, Portugal: Entidade Reguladora dos Serviços de Água e Resíduos (ERSAR) was hit by an attack on March 31, 2025
Dutch cybersecurity firm Eye Security first detected ToolShell exploitation in July, followed by CheckPoint Research’s further analysis.
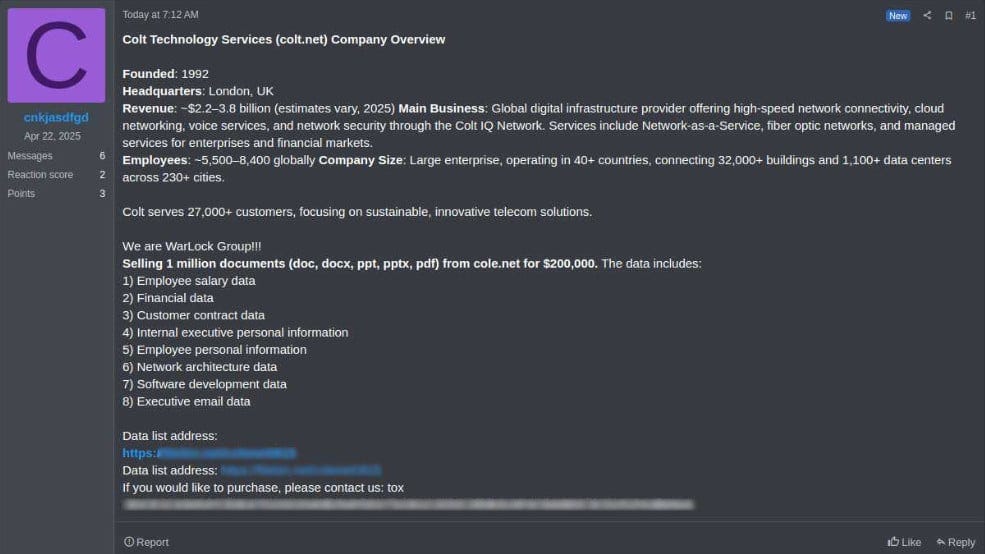
A threat actor using the alias ‘cnkjasdfgd’ and claiming to be a member of the WarLock ransomware gang claimed the attack and offered to sell for $200,000 a batch of one million documents allegedly stolen from Colt.
Several data samples have also been published to prove the validity of the files. According to the threat actor, the stolen files include financial, employee, customer, and executive data, internal emails, and software development information.
Although encryption details such as the use of AES or RSA have not yet been disclosed, Warlock employs modern double-extortion tactics. Limited encryption is used to maximize disruption speed, while exfiltrated data is published on leak sites to coerce payment.
Public reporting has not yet detailed whether the group aggressively targets recovery mechanisms such as shadow copies or backup agents, though the extortion-driven model and enterprise-scale intrusions strongly suggest these are likely components of the attack flow.
As of late July 2025, Warlock has claimed responsibility for 19 victims across sectors including government, finance, manufacturing, technology, and consumer goods. The group claimed at least 16 attacks in its first month, with nearly half targeting government entities.
No ransom payment structures or affiliate revenue shares have been confirmed, but broader industry data suggests government-related ransomware incidents in 2025 carried an average demand of $2.4 million. It is likely that Warlock customizes its ransom pricing based on the victim profile.
The timeline of activity shows rapid escalation: from forum promotion in early June, to deployment of ToolShell exploits in mid-July, to wide scale targeting by late July. Microsoft, Eye Security, and Check Point reported that Warlock and Storm-2603 compromised over 400 SharePoint servers across 148 organizations within weeks of the first wave of attacks.
In a response from the US Cybersecurity Infrastructure Security Agency (CISA), if anti-malware or endpoint detection/response is unable to be implemented immediately, their suggestion is to “disconnect affected products from service that are public-facing on the internet until official mitigations are available”. So…turn it off and back on, figuratively. This is not an ideal position for premier security agencies or globally dominant software providers to be in, and speaks to symptom of a deeper issue. Security fatigue.
In July, the American federal judiciary’s electronic case management system (CM/ECF) was compromised in a large-scale cyberattack. While the Administrative Office of U.S. Courts has publicly acknowledged the incident, its statement did not identify specifically what was accessed or compromised within the system. The judiciary did acknowledge, however, that the hackers appear to have accessed "highly sensitive non-public documents." The New York Times recently reported that an internal Justice Department memo disclosed that "persistent and sophisticated cyber threat actors have recently compromised sealed records”, attributing the cause to Russia. Attribution and specific tools and tactics will be explored at the end of this article.
Hackers compromised data from Canada’s House of Commons in a cyberattack exploiting a recent Microsoft vulnerability, according to a report from CBC News.
Staff were alerted to the data breach on Monday, as CBC News reported based on an internal email that explained the threat actor had accessed a database “containing information used to manage computers and mobile devices.”
It is not clear what the affected database was, or if it gave them access to sensitive information or House of Commons devices.
Data compromised by the threat actor includes “employees' names, job titles, office locations and email addresses, as well as information regarding their House of Commons-managed computers and mobile devices,” according to CBC News.
The specific vulnerability that allowed the attackers to break into the House of Commons network was not disclosed. It follows shortly after Microsoft issued an urgent alert after threat actors were discovered exploiting a zero-day vulnerability in on-premise SharePoint servers.
According to the internal email, the attack took place on Friday. The message implores staff at the House of Commons, alongside its elected members, to be vigilant to scams and follow-on malicious activities following the data breach. It does not indicate who may have been behind the attack.
Canada's Communications Security Establishment has repeatedly warned about the cyber threat facing the country from state actors, including China, Russia and Iran, as well as financially-motivated groups. The Canadian Centre for Cyber Security said last year that Chinese government-backed hackers had compromised at least 20 Canadian government networks since 2020.
Reporting aggregates indicate widespread exploitation since early July 2025, allegedly including:
U.S. National Nuclear Security Administration, U.S. Dept. of Education, Florida Dept. of Revenue, Rhode Island General Assembly, and government networks in Europe & the Middle East. More details will emerge as response and mitigation is ongoing.
A new Dragos report, published by Marsh Mclellan’s Cyber Risk Intelligence Center warns that global OT cyber risk exposure could exceed US$300 billion. Indirect losses, often overlooked in traditional models, account for up to 70% of OT (operational technology)-related breaches, with worst-case scenarios placing the global financial risk at $329.5 billion. Dubious hiring practices, reliance on remote and overseas work, longer hours, and a general lack of urgency is contributing to compromise in most systems today. People don’t care about protecting systems they’re cynical about upholding. Those responsible for networks at DoD, USAF, NSA, DARPA, Interpol, Google, Lockheed, Anduril, Palantir understand the risks involved in breaches of their systems, and are (ideally) philosophically, above legally inclined, to protect these systems. What we are seeing in the Canadian Parliament, and perhaps PACER, is a lack of vigilance, not for lack of tools or risk, but a lack of vision and a major risk miscalculation.
Technical Details:
SharePoint & Exchange act as “pivot points”, in-so-far that they straddle on-premises servers (often poorly patched) and cloud services (Microsoft 365, Azure AD).
CVE-2025-49704 – lets attackers run malicious code on the server.
CVE-2025-49706 – enables impersonation or spoofing across the network.
CVE-2025-53770 – a new, critical gap allowing remote code execution without authentication.
CVE-2025-53771 – a path-traversal weakness linked to spoofing and patch bypasses.
Customer Guidance for Sharepoint Vulnerabilities
Mitigation and Response Recommendations
Implement patches immediately and continue applying updates as they become available.
Rotate cryptographic material, such as ASP.NET machine keys, after patching.
Engage professional incident response teams if there’s potential or confirmed compromise.
Report incidents to respective jurisdictional cyber regulatory agencies and law enforcement
In hybrid setups, an attacker who compromises on-premises SharePoint or Exchange (usually through phishing, spear-phishing attacks) can often leverage trust relationships to escalate into cloud tenants, gaining centralized identity and file access. This means a single flaw in a local web service can grant enterprise-wide cloud access, far beyond the original machine. In cloud computing, data is aggregated for efficiency (such as one SaaS repository for all courts or all MPs) , but this creates a single point of catastrophic compromise. What a cascading cornucopia of catastrophic compromise we are seeing.




